Introduction to using Bitcoin Privately
BUT WHY ?
“Privacy is only for criminals”
Privacy is essential for personal safety: if bad actors can see your spending, income, savings, they can use that information to target/exploit you. They can tell exactly how much to try to scam you for.
Financial privacy is essential for human dignity. You don’t want your neighbour to know each time you spend your money.
Most importantly, financial privacy isn't incompatible with things like law enforcement. You can always keep records, be ordered (or volunteer) to provide them to whomever. None of this requires globally visible public records.
KYC/AML
https://disruptive-horizons.com/p/kyc-aml-destroying-world
Kyc is sold as being a good thing to stop bad actors But in reality its a threat to human freedom
Attack on our privacy. It is surveillance technology True criminals know how to avoid such policies
Really affects only small individuals, forces you to hand over personal information to a 3rd party to unlock/use your funds

PROBLEM STATEMENT
Bitcoin records txns on blockchain visible to everyone.
Sender address is known. Receiver address is known. Amount is known. Only identity of each address is not known.
The linkages between addresses can’t identify anyone by itself (since they are just Radom numbers) BUT if any of the addresses in a txns past or future can be tied to an actual identity, it might be possible to work from there and deduce all other addresses. (this is what chainanalysis firms get paid to do).
Bitcoin is pseudonymous. It doesn’t store anything apart from txn data. It’s the ecosystem/humans outside the blockchain that leak personal info.
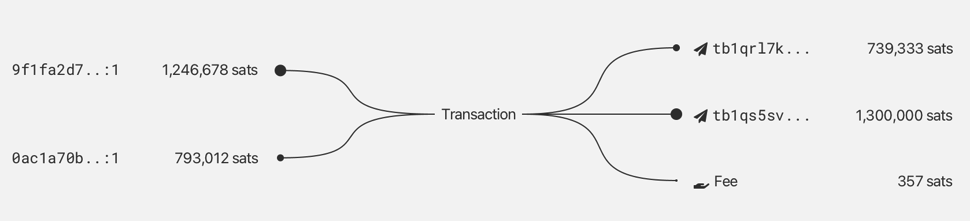

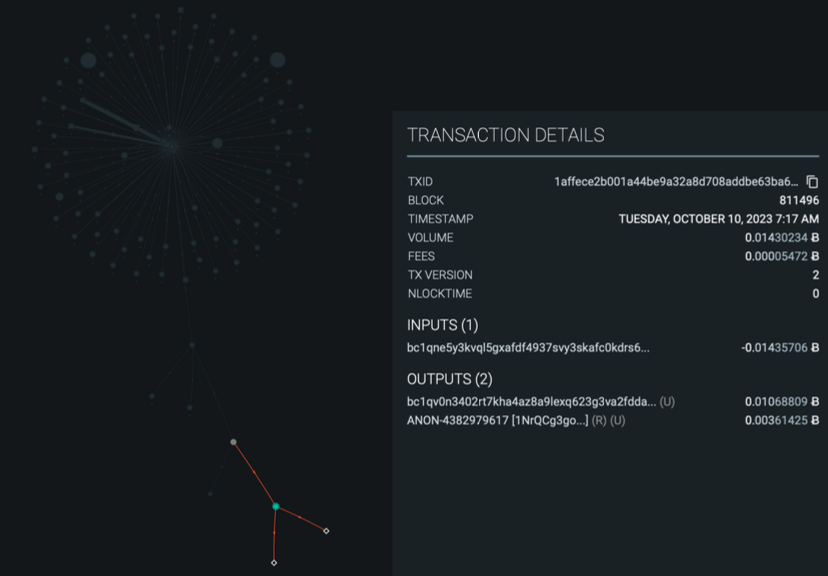
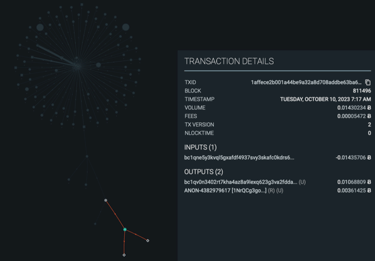
COMMON-INPUT-OWNERSHIP HEURISTIC & ADDRESS REUSE
Assumption that all inputs to a transaction are owned by the same entity.
Transactions with multiple inputs usually arise if the user's wallet does not have a single UTXO large enough to fulfil the user's payment amount.
Address reuse harms the privacy of not only yourself, but also others.
THREAT MODEL
Who are you hiding from?
How can this hypothetical adversary spy on you?
What information is important to you?
There is no magic software/hardware that will fix all your privacy concerns. Improving privacy requires a change in behaviour.
Being mindful of the places where you are revealing personal information such as phone number, email & address is a great start.
THREATS
Chainanalysis/transaction surveillance firms Kyc services
Apps and wallets that aren’t open source
BITCOIN PRIVACY - 2 PARTS
Where did the coins come from - source?
How do you store and spend them - learning & using the tools
SOURCING
Non Kyc services
peer to peer
“THE TOOLS”
Self custody
Node
Utxo management/coin control Coinjoins
Use Lightning for spending
Open source privacy enhancing services - Tails os, tor, vpn, email, messaging clients, phone os
SELF CUSTODY
Not your keys, not your coins
if you are buying from a no-KYC source then you will almost certainly require your own wallet
if you do not control your own keys, for eg if your bitcoin is held with a custodian, then you essentially have zero privacy. Whoever controls those keys has the ability to see all your funds and spend them as they see fit
Sparrow wallet, blue wallet, aqua, phoenix etc
NODE
No node = no privacy
Unless your chosen wallet is connected to your own node, you are trusting someone else’s
Trusting someone else’s node means that they can see - Every transaction you send, Every transaction you receive, All of your balances, In some cases every address in your wallet (even the currently empty ones)
parman node, start9 , Bitcoin core, raspiblitz
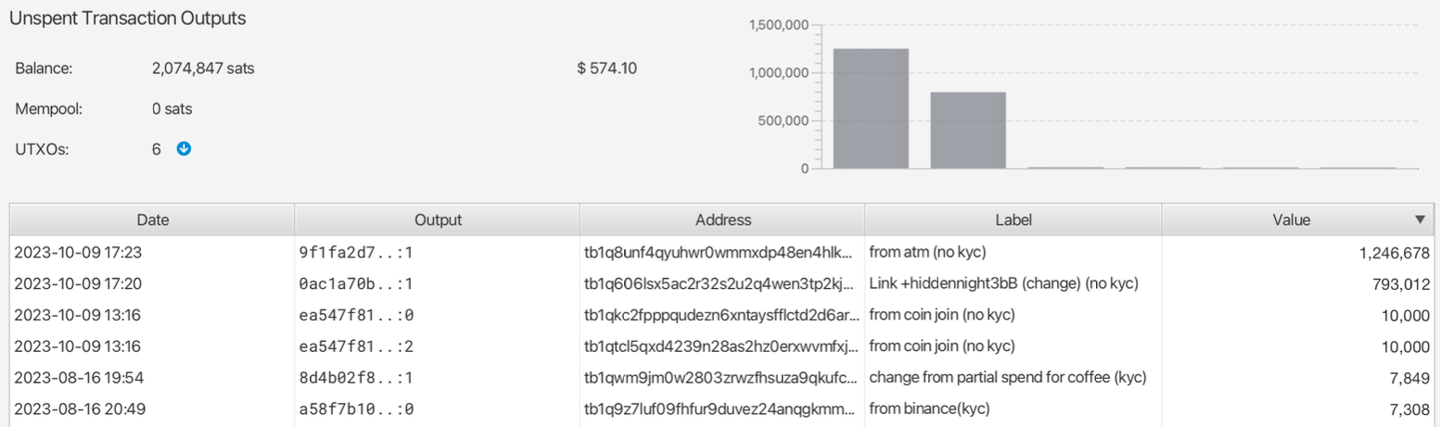
UTXO MANAGEMENT
Good labelling habits
Coin control - Mindfully spending utxos - manual selection before spending Segregating utxos used in a kyc service
NO address reuse
Avoid creating change addresses, for eg when opening a Lightning channel; spend entire utxo
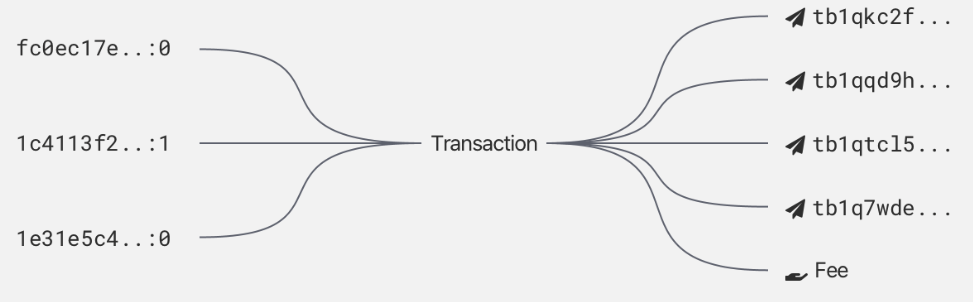
COIN JOIN
Two or more users pool their UTXOs together into a collaborative transaction. The way the transaction is constructed makes it very difficult for surveillance firms to know exactly which output belongs to which of the input owners.
At best anyone looking at the transaction can come up with a number of possible scenarios as to who owns which piece of bitcoin but they can never be 100% sure.
Now imagine you carry out multiple rounds of coinjoin one after the other, the transaction graph quickly becomes very confusing and impossible to track.
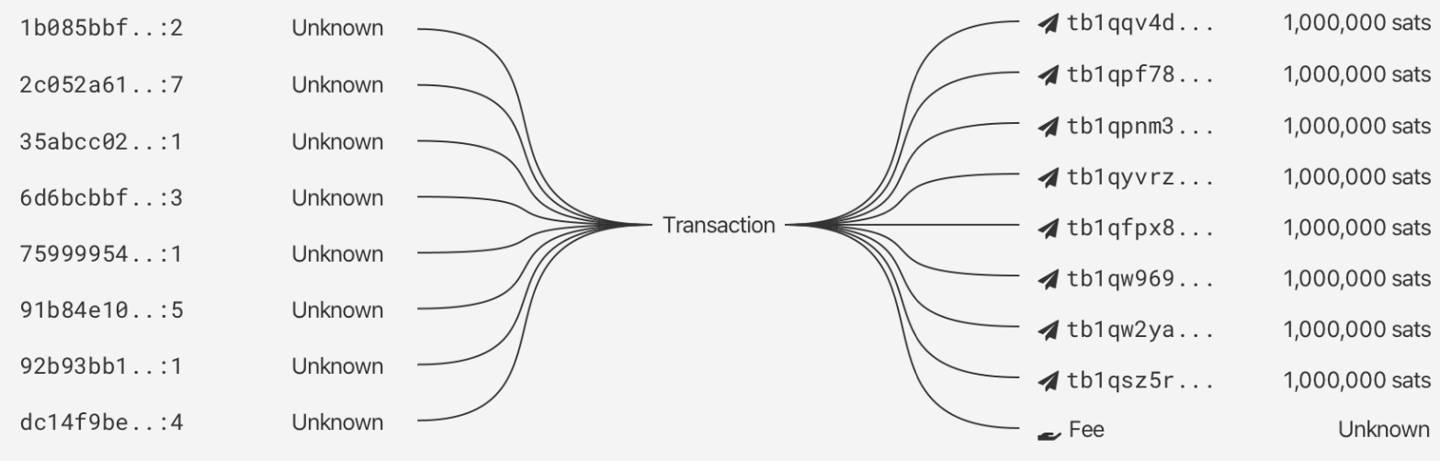


EXAMPLES
WHY NOT TO REUSE AN ADDRESS
You save in bitcoin. But use only one address.
All your bitcoin savings go to this same address, let's say it contains $1 million worth.
You buy a small amount of bitcoins to add to your savings, depositing in the wallet.
The person who sold you the bitcoins follows their trail on the blockchain and finds your wallet containing $1 million.
He mentions it to someone in a cafe or bar.
Word gets around. A burglar raids your home and knows exactly how much to demand.
EXAMPLES
WHY NOT TO REUSE AN ADDRESS
You want to accept donations in bitcoin, so you publish a single reused bitcoin address on your website.
Some people want to donate to you by buying bitcoins from an exchange and have the coins sent immediately to your donation address.
Unlucky for you, the exchange wants to block donations to you, so it does not allow people to send coins to your address.
The way to solve this is to avoid address reuse by displaying a brand new address to each visitor. That visitor can tell the exchange to send coins to that address. Because the address is new and unused the exchange will have no idea that it belongs to you, and so will be unable to block the transfer.
EXAMPLES
WHY NOT TO REUSE AN ADDRESS
You use a single Bitcoin address for all your earning and spending. Anyone you trade with can see a complete history of your finances.
Your landlord can see your salary, when he raises the rent he knows exactly how much to ask for.
Your shopkeeper can see your spending. Gossip gets around of how much you spend on beers and how little on church donations.
Your employer can see your spending. When you donate to wikileaks or another non-profit, your boss knows who not to trust.
PAYNYM
Bip 47
In order for two wallets to find each other, they need to use a unique identifier, much like a phone number. Each wallet can create this identifier deterministically, called a payment code. It’s similar to an xpub, except that no information about a wallet can be learned from it. In this sense, it is safe to share.
PayNym: +GrapheneOS
nov 2024 - New silent payments implementation is very interesting too - https://silentpayments.xyz/
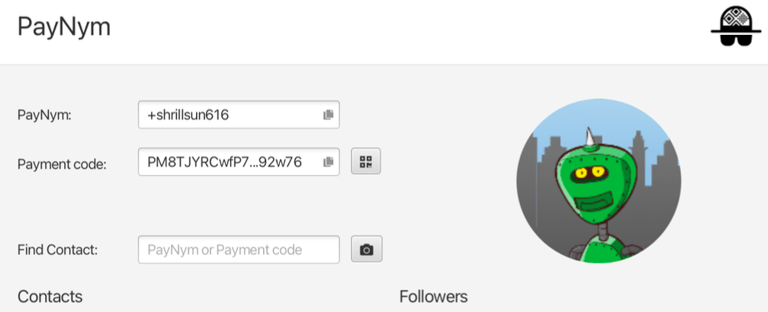
EXAMPLES
KYC EXCHANGES
You save in bitcoin. But also trade on an exchange which you reveal all your data to.
Mostly you buy coins but sometimes you sell. You only ever use this one exchange.
Regardless of any blockchain privacy technology you use, the exchange still knows all your trades and can find exactly how much bitcoin you hold at any time.
EXAMPLES
USING A BLOCKCHAIN EXPLORER
You receive a payment of bitcoin at one of your addresses.
You copy and paste the address into a blockchain explorer website and press Refresh until the incoming transaction reaches 3 confirmations.
The blockchain explorer website now knows that your IP address is very interested in that particular bitcoin address.
This is best avoided by using your own bitcoin wallet (backed by a full node) to tell you when payments have arrived and how many confirmations they have, without any other entity knowing.
Tor fixes this almost entirely but still reveals someone is very interested in that particular address
Why use an Open-source wallet with your own node
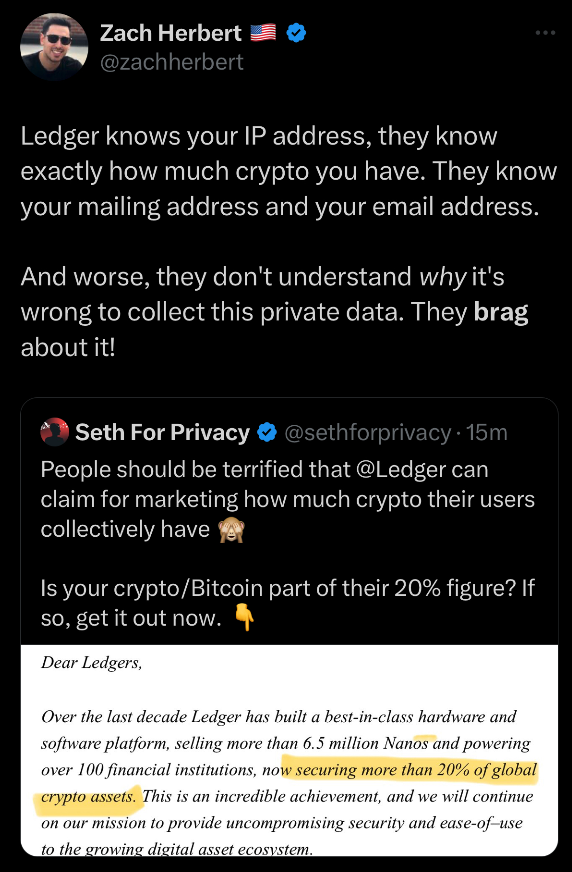
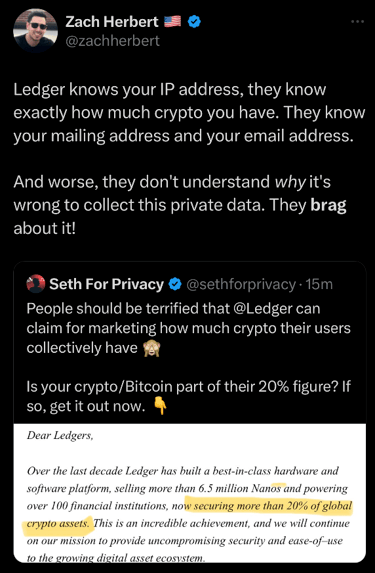
Summary
Self custody
Node
Utxo management/coin control - JAM ( join market) is great for learning Coinjoins
Use Lightning for spending
Open source privacy enhancing services - Tails os, tor, vpn, email, messaging clients, phone os, silent.link
Every action you take on your closed sourced phone/app gets stored in “someones” database (big tech)
Bitcoin txn history is forever
“Cypherpunks write code. … We know that software can’t be destroyed, and that a widely dispersed system can’t be shut down.”
-A Cypherpunk’s Manifesto by Eric Hughes
